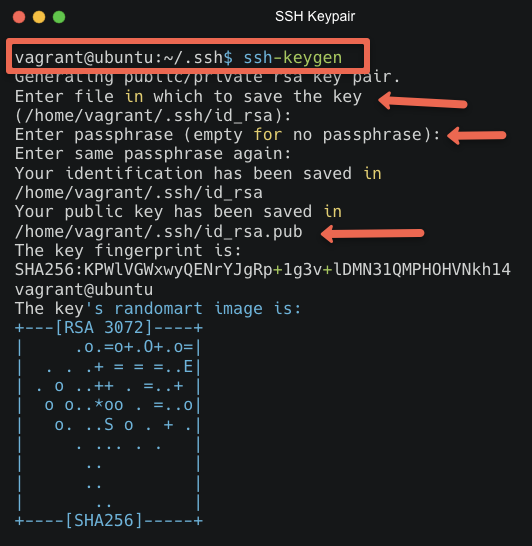
Electronics | Free Full-Text | Multiprotocol Authentication Device for HPC and Cloud Environments Based on Elliptic Curve Cryptography
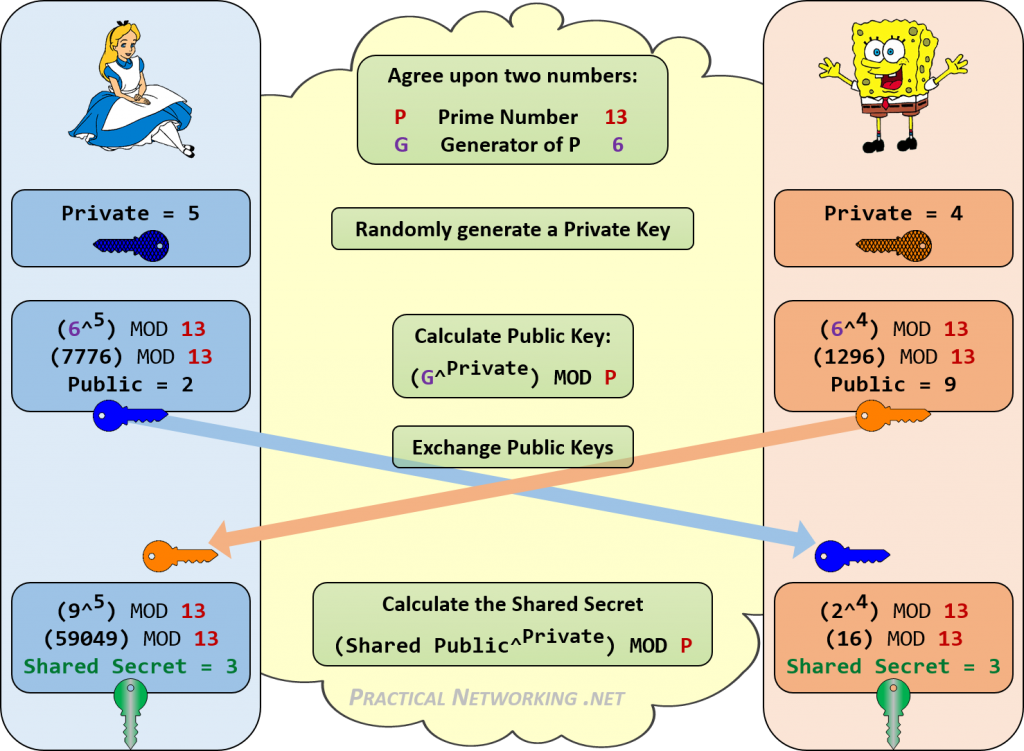
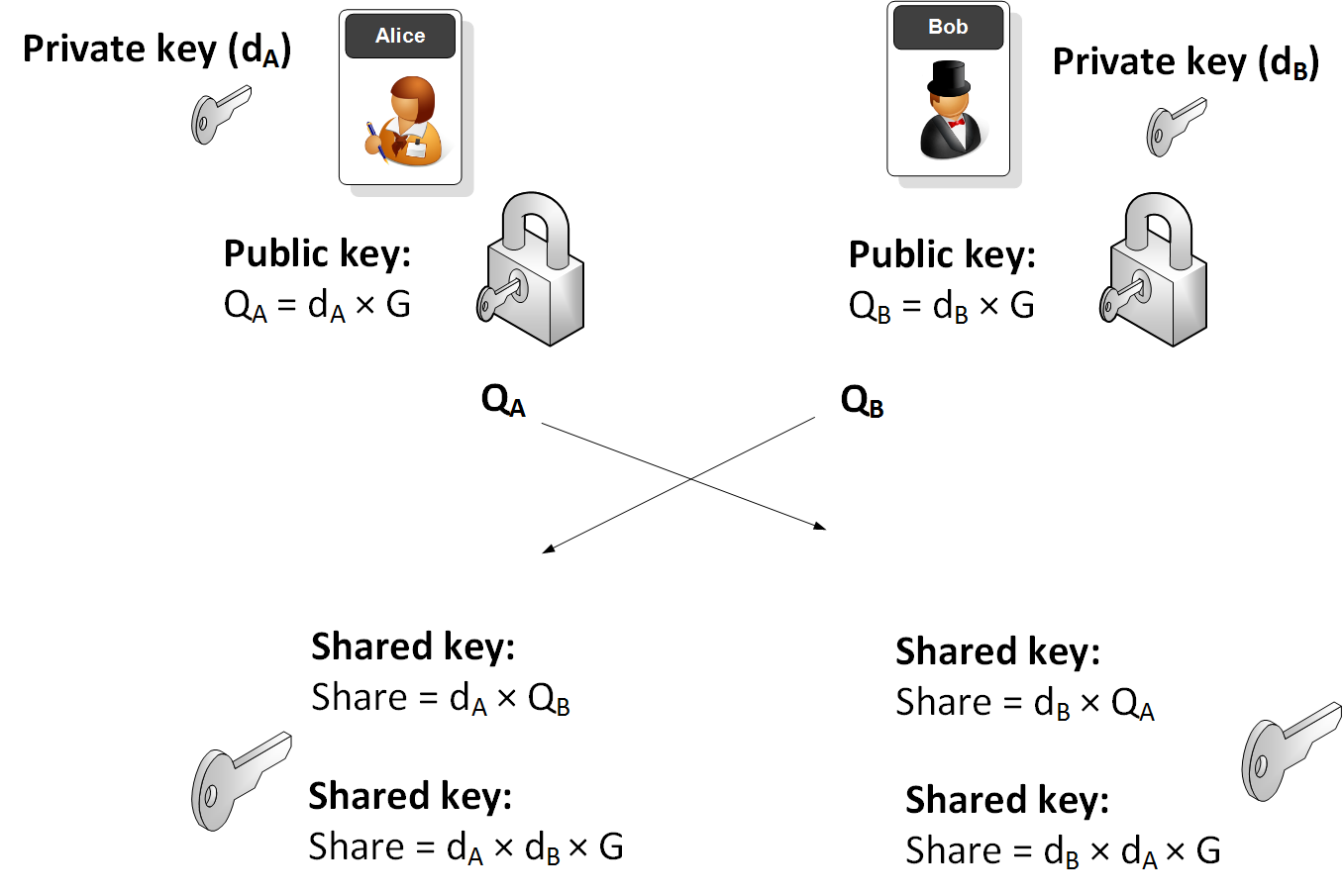
Implementing Elliptic-curve Diffie–Hellman Key Exchange Algorithm using C# (cross-platform) | David Tavarez